 Home >
Home > 
Why is Two Factor Authentication Important
As data breaches and cyberattacks grow in number and complexity, users should secure their data by implementing advanced security measures. Using two-factor authentication (2FA) is a great way to enhance user security.
Using a strong password isn’t enough to keep online accounts and data safe in the event of a data breach. 2-factor authentication allows users to add another security layer to their personal information.
- Two-factor authentication: Its purpose and functioning
- Understanding identity and access management
- Authentication factors: What are they?
- The mechanics of two-factor authentication
- So, why use two-factor authentication?
- Tools for 2FA
- Components of two-factor authentication
- Varieties of two-factor authentication solutions
- 2FA and Stands Adblocker
- Conclusion
- FAQ about 2FA
Two-factor authentication: Its purpose and functioning
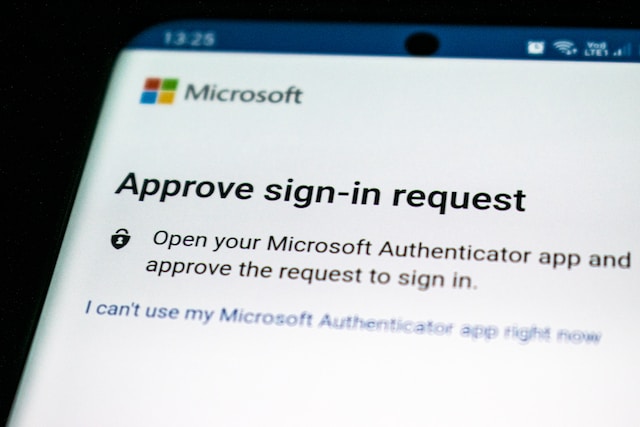
To better understand why two-factor authentication is important, we need to know what it is and how it works. 2FA is a security process that requires two different methods to identify a user’s identity. Only then can it grant them access to their accounts and information.
It’s easy for hackers to steal usernames and passwords during a data breach. However, people who use 2F authentication have an additional layer of security that makes it harder for cyber-attackers to gain unauthorized access to data.
These two verification methods, or authentication factors, neutralize the risks associated with compromised passwords, which is essential for web security. 2-factor security measures protect against phishing, password brute-force attacks, social engineering, and attackers exploiting stolen credentials.
Understanding identity and access management

Identity and access management (IAM) is a cybersecurity and business discipline that manages user identities and access permissions in complex, multi-cloud environments, such as corporate networks.
An IAM initiative aims to ensure that the right users and machines access the right resources and assets at the right time and for the right reasons, keeping unauthorized and fraudulent access at bay.
Identity and access management solutions perform two important tasks. First, they confirm the user’s identity by authenticating their credentials using a preexistant database. Then, they grant the users the right level of access, instead of allowing everyone to access the entire software suite.
Using two-factor authentication in an identity and access management program is considered a good practice as it adds another layer of security.
Authentication factors: What are they?

What 2-factor authentication needs to properly work is a combination of any two types of authentication factors. These factors are particular pieces of information that users must provide to verify their identity. The type of factors used may vary between users or companies, but they usually get to choose from:
- Knowledge factors. These factors verify user identity by requesting something only they would know. This could be a password, a personal identification number (PIN), or the answers to a series of security questions.
- Possession factors. Possession factors identify users based on something that they physically carry on their person, such as an ID card, a smartphone app, a security token, or any other mobile device.
- Inherence factors. These factors, also known as biometric factors, involve aspects that are inherent to the user’s physical attributes. They can include fingertip scanning, facial and voice recognition, or even behavioral biometrics, such as gait, speech patterns, and keystroke dynamics.
- Location factors. Certain 2-factor security solutions confirm the identity of a user based on their location. They do this by monitoring the IP addresses of the original users and tracking the geographical source of authentication attempts based on GPS data.
- Time factors. Based on the assumption that users must authenticate within predictable time ranges, verifying their identity is possible by allowing them to log on to their accounts only in restricted time windows.
The mechanics of two-factor authentication

The mechanics of two-factor authentication differ based on the type of factors used, however, the basic steps are always the same. Typically, a 2-factor security transaction involves:
- The user logging on to their account, website, service, or application using a username and password combination
- The authentication server recognizing the match and validating the combination, making the user eligible for the second factor
- The user providing the second form of authentication established (a PIN, a fingertip, or a security code, for instance)
- The authentication server validating the second form of authentication and granting the user access to the account, website, service, or application in question
This process might not happen every time a user tries to authenticate themself. Some organizations request these types of verifications every few days, while others require authentication each time a user logs in from a new device.
So, why use two-factor authentication?

Enhanced Security
The most important reason to use two-factor authentication is the fact that it adds an extra layer of security. Cyberattacks are more common and complex and it's relatively easy for hackers to access usernames and passwords. With 2FA, however, they would still need an additional factor to access the account.
Protection Against Phishing
The most common way hackers attempt to access user accounts is through phishing attacks, hence the importance of two factor authentication. Even in the event of a user falling for a phishing scam by, for instance, opening an email link to a malicious website, the hacker still doesn’t have access to the second authentication factor.
Users who take the time to learn how to use 2FA can use it to fight phishing scams by adding an extra layer of protection after cybercriminals enter their passwords.
Compliance
Using 2FA is a way for companies to take important steps to protect sensitive and personal information and comply with data protection and privacy regulations.
For instance, the Payment Card Industry (PCI) Data Security Standards (DSS), used to secure credit card transactions, mandates 2FA as a prerequisite to receiving the certification required for certain types of transactions.
Convenience
2-factor security might seem like an extra step in user authentication, but it is convenient in the long run. By using 2FA, users don’t need to change their passwords as frequently, and several authentication factors are quick and easy to use.
From the administrative point of view, 2FA simplifies the process of managing many different accounts and frees IT teams from consistently handling password resets.
Cost-Effective
2FA is a cost-effective security measure. The cost of implementing a 2-factor security measure is much lower than the costs associated with mitigating a data breach or cyberattack.
Tools for 2FA

There are several tools for 2FA available on the internet, depending on the 2-factor security mechanism that companies and users want to implement. A few of the most popular include:
- Hardware tokens. These tokens are the oldest form of 2FA. They create new numeric codes every 30 seconds and users have to input the code that appears on their device whenever prompted. Other versions of this device come with a USB port that users can plug into their computer, directly. While hardware tokens are easy to carry, they’re also easy to misplace.
- SMS text or voice message. This type of 2-factor security requires only access to a personal phone. After completing the first part of the authentication, the website or app asks the user whether they’d prefer a text message or a phone call to receive their verification code. This method is quick and easy to use, however, 2FA via SMS is not that safe anymore.
- Authentication apps. These apps are directly installed in the user’s smartphone or laptop, meaning that only the person with access to these devices can access the security code. Authentication apps generate time-based one-time passwords (TOTP) that users must use when prompted.
- Push notifications. Instead of creating single-use passwords, certain apps send users a push notification whenever they’re trying to log in to their account. To verify their identity, users simply need to touch their screens.
Components of two-factor authentication
There are two components of 2-factor authentication. These components comprise two different types of authentication factors. True 2-factor security measures use, for instance, a knowledge factor along with a possession or an inherence factor.
People commonly what 2-factor authentication is with dual authentication. The latter also involves 2 forms of identity verification but the authentication factors are usually the same. In a dual authentication solution, users often use a username-password and are then prompted to answer a personal question, which are both knowledge factors.
Varieties of two-factor authentication solutions

There’s a wide variety of 2FA solutions available on the market. A few of the most popular include:
CISCO Duo Security
Duo Security’s 2-factor security system enables users to authenticate their identities using the Duo mobile app, through push notifications. This app integrates with iPhone and Android smartphones, as well as with the Apple Watch.
Duo also works with universal second-factor authentication tokens, FIDO-supported hardware tokens, mobile security codes, USB devices, and biometric controls, such as FaceID. Administrators can configure adaptive authentication policies based on user location, devices, and roles.
Okta Adaptive Multi-Factor Authentication
OKTA’s multi-factor authentication solution is great for companies as it allows the authentication of employees, partners, and customers alike. The admin portal is easy to use, encouraging the organization to use two-factor authentication.
This solution has a minimal impact on user productivity as it only prompts them to authenticate their identity whenever they log in at a new location, on a new IP address, or a new device. It offers a wide variety of authentication methods such as security questions, one-time security codes, SMS 2FA, mobile app authentication, and biometrics.
RSA SecurID
RSA SecurID is the best option for companies that want to move on from legacy hardware and software tokens to mobile authentication solutions. Its main focus is providing convenience for end users.
This 2-factor security solution offers a range of authentication methods including biometrics, one-time passcodes, SMS texts, and push notifications. It also supports hardware and software tokens to ensure maximum security.
2FA and Stands Adblocker
The reason why two-factor authentication is so important is the security it offers in an environment where cyberattacks are increasingly common and complex. Because we understand the importance of cybersecurity, we’ve created a free Adblocker to keep users safe while navigating the internet.
The Stands Adblocker blocks ads in Google Chrome, enhancing browsing efficiency by stopping disruptive ads, protecting users against potential malware, and ensuring a more secure online environment. It also protects the user’s privacy, by preventing ads from collecting the user’s browsing activity and other types of data.
We also provide a version of our service for Android devices. Our Android AdBlocker provides a great additional layer of security, reducing the chances of getting your device infected with viruses and spyware, while still maintaining site functionality and appearance.
Conclusion
Using two-factor authentication solutions is a great way to enhance data security and protect sensitive information. It combines the use of two different types of authentication factors which can include things users know, things they possess, or things that are physically inherent to them.
The main benefits of using 2-factor security measures include protection against many types of cyberattacks and phishing scams, convenience, and cost-effectiveness. Many tools are available for 2FA such as hardware tokens, authentication apps, and push notifications.
For an added layer of security, we encourage users to try Stands Adblocker. It offers an efficient browsing experience while protecting users from malware, viruses, and spyware that might come from malicious ads.
FAQ about 2FA
How do I enable 2FA for added security?
The process of enabling 2FA for added security depends on the solution you’re trying to use. In an application that manages 2FA codes, such as Google Authenticator, enabling 2FA is as easy as going to the account settings and clicking on “Enable two-factor authentication”.
How can I configure 2FA?
After enabling 2FA users can configure it by choosing the authentication factor they wish to use. For instance, they might opt to receive security codes via SMS text or phone call, verify identity through push notification, or receive a passcode on their authenticator app.
What are some benefits of implementing 2FA in online accounts?
Some benefits of implementing 2FA in online accounts include fraud and identity theft prevention, streamlining the login process, reducing operational costs, adding more security layers, and meeting security regulatory compliances.